The next evolution in Office365 phishing campaigns
It comes as no surprise that Office365 is one of the most targeted services for phishing attacks worldwide. Credentials for enterprise Microsoft accounts are some of the most valuable for threat actors who can leverage them for a number of activities with this initial access vector. This ranges from stealing emails, business email compromise (BEC), to internal spear-phishing and malware attacks.
The latest wave of Office365 credential harvesting attacks involve multiple steps. This includes the phishing email itself, a malicious URL, a legitimate document hosting service (such as *.clickfunnels[.]com or *.larksuite[.]com), and the fake login page. These kits are also known as a "LogoKit" for being able to dynamically alter the page's appearance based on the domain in the target's email address.
Demo of how this works: https://app.any.run/tasks/e59d36ba-5a2c-49e3-8b59-8044bf593689/
This campaign typically leverages free domains using multiple gTLDs - namely .tk, .gq, .ml, .ga, and .cf - and hosts them on NameCheap servers (AS22612).
(Fig. 2 - Analysis of the infrastructure behind the high number of Office365 landing pages)
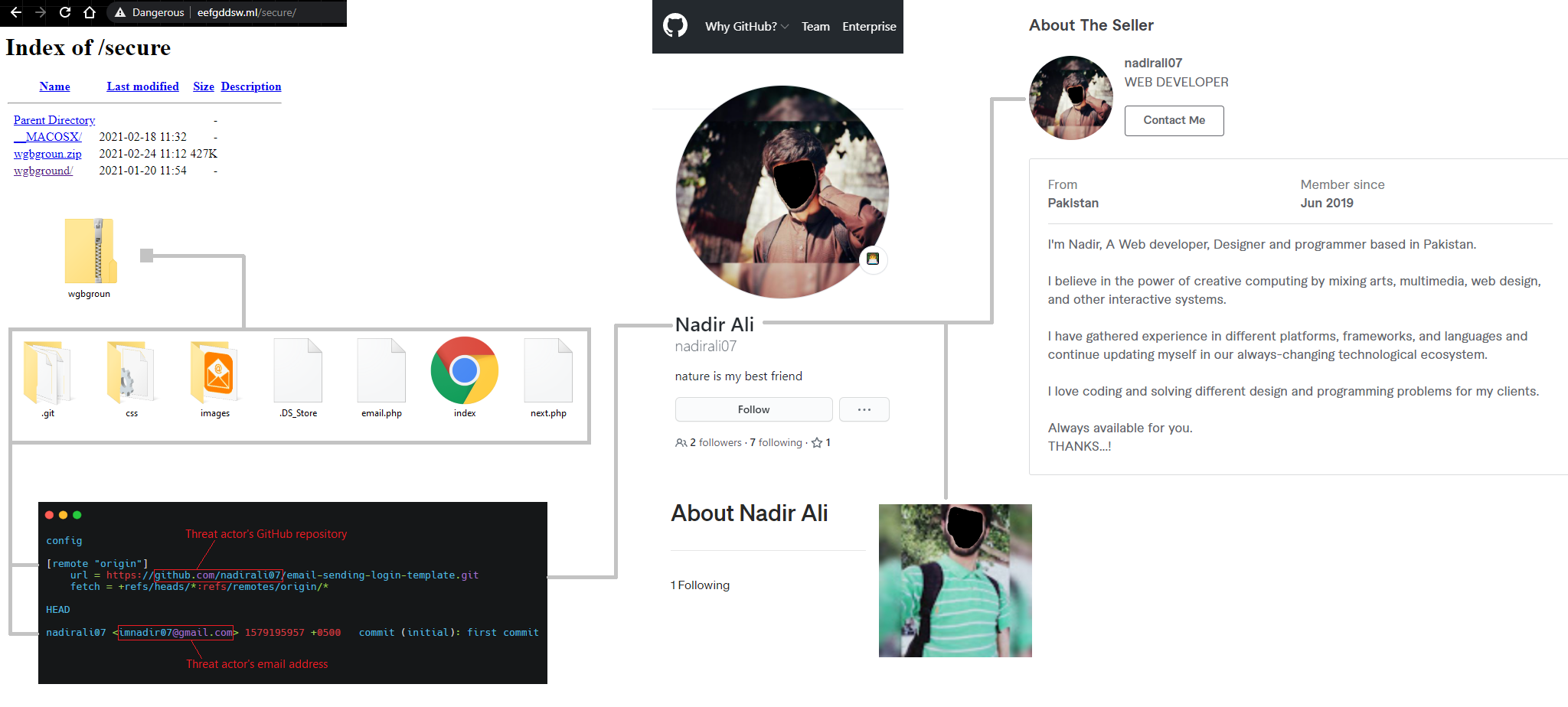
Fortunately, the ZIP archive of the phishing kit used in this campaign was located, sitting in an open directory. Analysis of the PHP and JavaScript behind this phishing kit revealed how the data is being collected and exfiltrated:
A number of details were left in the phishing kit which enabled me to pivot, using OSINT techniques, to the threat actor's profiles online. This is likely either the threat actor who is stealing the credentials for illegal gains or the individual who coded the phishing kit.
From investigating open sources, other security researchers have run into this threat actor in the past. They have been actively running phishing campaigns for over a year. (1, 2, 3)
Threat Intelligence:
Next, it is possible to track this campaign via open source tools. The phisher uses a number of TTPs which we can use to monitor for signs of this campaign. Although, by disclosing the threat actor's techniques it may force them to change their tactics but, by doing so, it incurrs costs to the adversary.
The URLscan assets we can use to track this campaign:
- The directory "/wgbground/" - https://urlscan.io/search/#filename%3Awgbground
- The directory "/wggebbma/" - https://urlscan.io/search/#filename%3Awggebbma
- The image "vzbuQ.jpg" - https://urlscan.io/search/#filename%3AvzbuQ.jpg
- *.larksuite[.]com
- *.clickfunnels[.]com
- DGA infrastructure - https://otx.alienvault.com/pulse/603bbb633e873fbd7fc45337
- https://blog.bushidotoken.net/2020/10/analysing-phishing-c-server.html
- https://blog.bushidotoken.net/2020/11/one-persistent-phish.html
- https://blog.bushidotoken.net/2020/05/gone-phishing.html
- https://blog.bushidotoken.net/2020/06/threat-actors-phishing-airbnb-users-for.html
- https://blog.bushidotoken.net/2020/03/using-image-hashes-to-find-phishing.html