Geopolitical Cybercrime: LockBit attack on the ICBC
What happened?
On 8 November 2023, the Industrial and
Commercial Bank of China (ICBC) was attacked
by the LockBit ransomware group. The ICBC is one
of the world’s largest banks and is a Chinese state-owned asset. Financial media sources,
such as the Financial Times and Bloomberg reported that the wider
financial system was impacted
as certain trades on the US Treasury market were unable to clear because of the
LockBit attack. Reuters also reported
that the impact on ICBC’s network was significant enough that the bank had to resort to manual
processes to perform trades in the billions of US dollars.
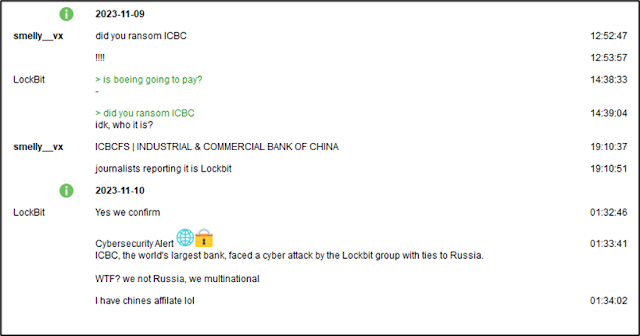
At the time of writing, ICBC has not
appeared on LockBit’s data leak site. However, in a conversation over the TOX messaging
application with VX-Underground,
a LockBit representative did confirm that they attacked ICBC.
Additional context
LockBit
is currently the most prolific
ransomware group in the world. They claim to be a “multinational”
organization and the threat actor “LockBitSupp”
(who may even be reading this blog, hello 👋) maintains a semi-public persona on the Russian-speaking
underground forums and often interacts with journalists and researchers
over TOX messenger, an end-to-end encrypted chatting application. Because of this semi-public persona,
LockBit is able to recruit dozens, possibly more than a hundred, affiliates to use
their Ransomware-as-a-Service (RaaS) platform to launch attacks.
LockBit’s claim that they are “multinational” is reasonably true. LockBit affiliates have been arrested or reported on in multiple countries outside of Russia, including Canada, the US, and China. However, it is not yet clear or publicly known which affiliate group is responsible for the attack on the ICBC.
- In November 2022, a Russian and Canadian national, Mikhail Vasiliev, was arrested after joint FBI operation while still having access to the LockBit affiliate panel.
- In June 2023, another LockBit affiliate who is a Russian-Chechen national, Ruslan Magomedovich Astamirov, was also arrested in Arizona, the United States, of all places.
- In January 2022, Microsoft confirmed that LockBit also has a Chinese-speaking affiliate group, which it tracks as DEV-0401 (or Storm-0401 now). Plus, Secureworks noted in June 2022, that DEV-0401 (aka BRONZE STARLIGHT) also has numerous technical overlaps with the Chinese Ministry of State Security-affiliated threat group known as APT10 (aka BRONZE RIVERSIDE).
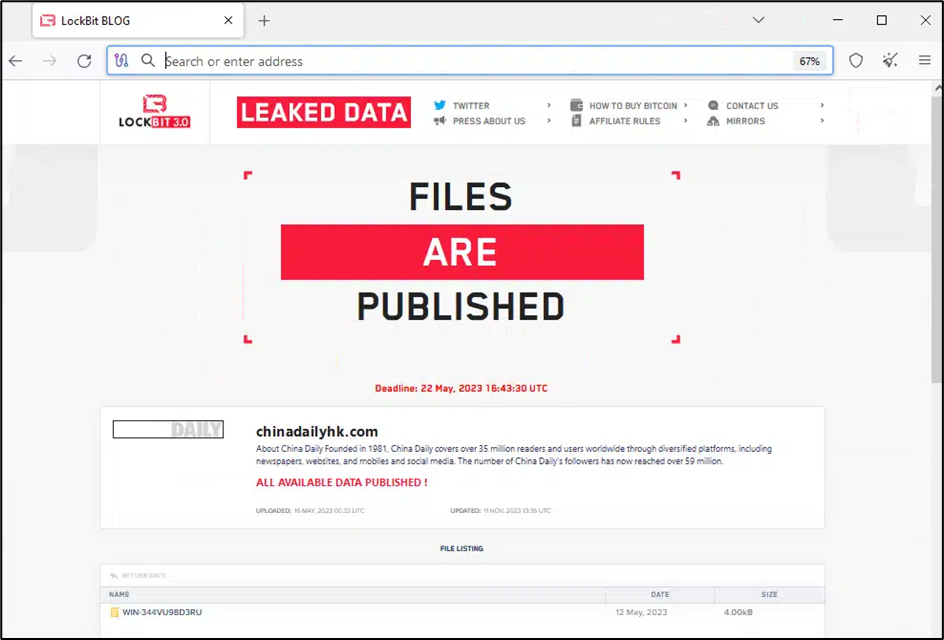
The ICBC is also not the first Chinese state-owned asset hit by LockBit. In May 2023, LockBit also added China Daily HK as a victim
to its infamous Tor data leak site. This victim was notable as it is an
English-language daily newspaper owned by the Central Propaganda Department of
the Chinese Communist Party (CCP).
It is also important to remember that China is by no means innocent when it comes to launching cyber-espionage campaigns against Russia. While not destructive in nature, Russia likely does not appreciate them.
- In April 2022, Secureworks shared that BRONZE PRESIDENT (aka Mustang Panda), a Chinese cyber-espionage group, launched a spear-phishing campaign against Russian officials, using Russia’s invasion of Ukraine-themed lure documents.
- In early May 2022, Google TAG disclosed that Curious Gorge, a group TAG attributes to China's PLA SSF, targeted Russia, in long running campaigns against multiple government organizations have continued, including the Russian Ministry of Foreign Affairs. Google TAG also identified additional compromises impacting multiple Russian defense contractors and manufacturers and a Russian logistics company.
- In mid-May 2022, Russian cybersecurity firm Positive Technologies (a firm sanctioned by the US for working with the Russian foreign intelligence service or SVR) also shared a report about a Chinese state-sponsored threat group, dubbed Space Pirates, which targeted IT services, aerospace, and electric power industries located in Russia, Georgia, and Mongolia in an intelligence-gathering campaigns.
The Implications
The fallout from this
LockBit attack on the ICBC has broad geopolitical implications. It directly creates
tension and causes issues between China and Russia. This is the second significant Chinese state-owned asset that a Russian ransomware gang has attacked in 2023. It is
interesting to observe a Russian state-permitted ransomware gang attack a key
ally of Russia, and especially one of China’s largest assets. The ICBC attack
has likely caused significant financial losses directly for CCP members in
Beijing, who are powerful individuals that will likely demand answers from the
Kremlin.
The question is, has
Russia lost control over their ransomware groups? Or was this a state-directed
attack on China in retaliation for the numerous cyber-espionage campaigns
targeting Russian government entities? To be honest, we may never know the
answer, but it is interesting to think about.
It is difficult to predict the future, but perhaps we may see the Russian FSB may perform another round of token arrests, similar to what happened to REvil, and takedown LockBit as a favour to their Chinese allies reeling from the ICBC attack. Nevertheless, organizations of all sizes shall have to continue monitoring LockBit campaigns in the foreseeable future. The ransomware group is still around for now, but hopefully will go the way of REvil or Ragnar Locker soon.