Fake Steam Desktop Authenticator App distributing DarkCrystal RAT
The threat actors distributing the fake version of SDA use two techniques that are effective when paired together: Site Cloning and Typosquatting.
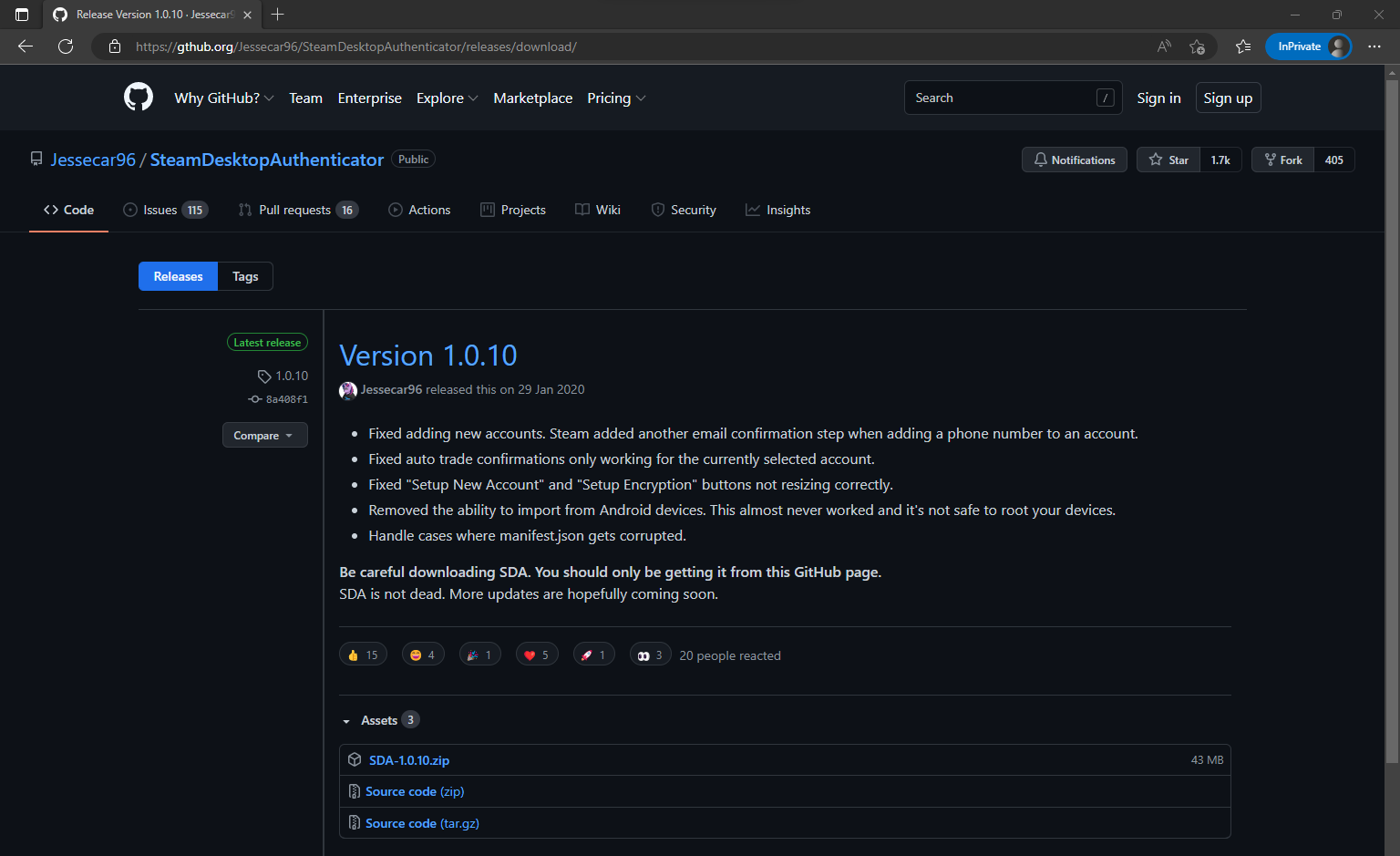
If a user visits the fake version of the site then they can download a 135.08 MB ZIP file of the "SDA-1.0.10.zip" app, which I've added to VT already here: VirusTotal - File - 132985696e0932e068afc7c8c93c9f67565e12434eb860d504413e948a06d3fb
Here is an example of the malicious version of the Steam Desktop Authenticator.exe inside one of these ZIPs VirusTotal - File - d65fdeff64de39aecb66d54b9507dbda3a73b35d58311294d5867117e93e0b48
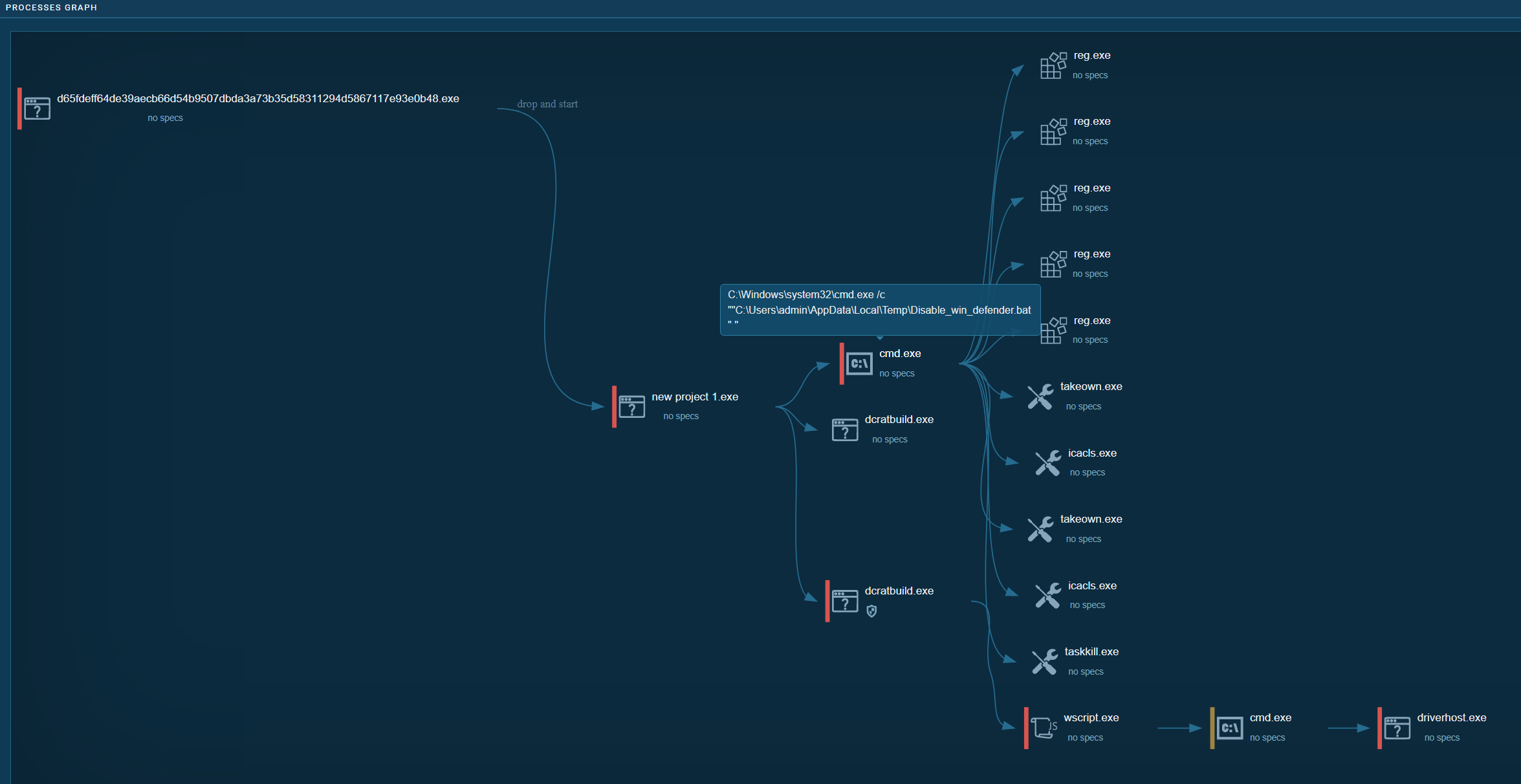
If executed, we can see a process tree involving multiple malicious Commands (using a .BAT script) that ultimately disables Windows Defender and runs DCRAT.
Figure 3: Malicious SDA app process treee
The Batch script "Disable_win_defender.bat" does what it says on the tin really. Added to VirusTotal here: VirusTotal - File - eb8ece6e556186008fd841095441a97406793a5611a2a6d9f50182fe649d8047
In short, it modifies registry keys to disable Defender Policies, deletes the Run key, and kills the SecurityHealthService.exe running process.
The final step and main aim of this fake app is the delivery of the DarkCrystal RAT (aka DCRAT). Added to VirusTotal here: VirusTotal - File - 83e90e41f6fdf724781c664e06f8172ee3e5a142f147a7fe355d5bf741cabd75
Additional context on DCRAT is available from BlackBerry (see here). In short, it's a commodity crimeware tool offered on various underground forums and Telegram channels, that can be bought and deployed by any aspiring cybercriminal.
Infrastructure Analysis
The three URLs I found related to this campaign all use the same technique to pose as the SDA app:
- hxxps://gthub[.]org/Jessecar96/SteamDesktopAuthenticator/releases/download/1.0.10/SDA-1.0.10.zip
- hxxp://glthub[.]org/jessecar96/steamdesktopauthenticator/releases/download/1.0.10/sda-1.0.10.zip
- hxxps://gllthub[.]com/Jessecar96/SteamDesktopAuthenticator/releases/download/1.0.10/sda-1.0.10.zip
The registrars, available registrant data, and AS of these domains and other related to this campaign are as follows:
gthub[.]org
Registrar: REG.RU LLC
Created on 2021-11-26
AS13335 CLOUDFLARENET
https://urlscan.io/result/08832cc7-c855-4d33-b707-4720552c5c9e/
glthub[.]org
Registrar: GoDaddy LLC
Created on 2021-11-26
AS13335 CLOUDFLARENET
https://urlscan.io/result/860ae730-65ff-4fe2-8127-c5dccda9400e/
gllthub[.]com
Registrar: REG.RU
Registrant: Maksim Erasov | erasmaxonl@mail.ru
Created on 2023-02-27
AS13335 CLOUDFLARENET
https://urlscan.io/result/fce3d43a-dbaf-4d89-892b-9ee0f477448e/
steamdesktopauthenticator[.]net
Registrar: REG.RU
Registrant: Artyom Mihaylov | atermmihailov35rus@mail.ru
Created on 2023-02-21
AS13335 CLOUDFLARENET
https://urlscan.io/result/91e512e9-0b12-4778-a3cc-1e16e93cb47f/
steamdesktopauthenticator[.]org
Registrar: REG.RU
Created on 2023-02-26
AS13335 CLOUDFLARENET
https://urlscan.io/result/d2397e76-57dc-495c-b122-824afad5cc93/
steamauthenticator[.]net
Registrar: REG.RU
Registrant: Petr Abramov | abramovpetr4030@mail.ru
Created on 2022-02-25
AS13335 CLOUDFLARENET
https://urlscan.io/result/46ddf176-8131-4033-8b90-85542b362389/
steamdesktopauthenticator[.]ru
Registrar: REG.RU
Created on 2022-09-06
AS13335 CLOUDFLARENET
https://urlscan.io/result/96db56a5-bafc-4481-98ba-443ebfe16d9f/
Indicators of Compromise
Steam Desktop Authenticator.exe
d65fdeff64de39aecb66d54b9507dbda3a73b35d58311294d5867117e93e0b48
d65fdeff64de39aecb66d54b9507dbda3a73b35d58311294d5867117e93e0b48
c4c8ef548db152990df000a2f759405b2b76ac078f1d34797a0e73b959fd9839
c098f6faf6b96b47d13e716f31f01b6dfc50cf900bec41db4c6b924b9f8dd38b
2ff83f329fb099b7ad4e8ba3e00c4dc076249629d6351cbde64abf566119286a
2439e397f7004d283cd665723c52ae0c37a7945767e26cc3cad6f227f77e5de6
f5222b6a69fd7855603d7186ca203e892783ee8b7418268065e58465028fc750
ad3bf4b59f06e3b22d21beaecff16fa7033517e5b563d98f8eb8537e9ecaf814
45dc2cded5af3330e4431c4ba0024c9f95043ba10b0be4cbadc39ae2627073d4
9a8b8ce801abc9bd32756c8c26975014a164363df11aafea082b15f83a024ec6
ca105bf5f645fe7ef2eb9b2a1a65bd40311263bd8c8d312dd639faff2795b37c
6b77f4c7b0d52054e7eaecb146112364c9813b0d780641ff0e688ee814c245e8
de284b2aee31d0d97d498fc8c331629e0d86a1143a813707e10787a4965a9147
d34ad66798bfd506ce4826b702225ef05cf76e609f144f3f3e51a0b0f5ec4385
ca8d61ceb3a84462db8188323c460a142e579850b7dbdbac588d5437098d7735
24651012ee2b948702d094f6bc53d23eb47fda1be535f3f168eeb4b5e249d7c1
d99138831a9b3b8c0062d0d16381af10ab73f3eb27a4814158bfc89e2e220dd1
d567bb8aa23cdd500199d25604d2d1e37353f02316ecc9fabb3711aad145affc
cae9404a614a69bd5a3d52e57968d0c1a5ed9da0b1f9e5069c49e1bb0af02dd7
7fb3a5bc2a1d9d96f1f998d15cad23b8ad9121de1569fe91491a70494353625c
c35611bc612a372acd517fc027ebdad40c794179b6f845661c0c861344a7a3fd
Disable_win_defender.bat
eb8ece6e556186008fd841095441a97406793a5611a2a6d9f50182fe649d8047
DCRatBuild.exe
83e90e41f6fdf724781c664e06f8172ee3e5a142f147a7fe355d5bf741cabd75