Brute Ratel cracked and shared across the Cybercriminal Underground
A short blog to document the proliferation of an advanced commercial penetration testing tool among cybercriminal threat actors across various Russian- and English-speaking underground forums.
What?
Available since December 2020, Brute Ratel C4 (aka BRC4) is one of the hottest new Red Team frameworks to hit the scene. It is similar to other frameworks such as Cobalt Strike but is uniquely concerning for its focus on evading endpoint detection and response (EDR) and antivirus (AV) tools. A technical analysis of BRC4 has already been provided by Palo Alto Networks Unit42 (see their blog here).
At 19:59:20 UTC on 13 September 2022, an archive file called "bruteratel_1.2.2.Scandinavian_Defense.tar.gz" was uploaded to VirusTotal. This file contains a valid copy of BRC4 version 1.2.2/5.
On 28 September, the developer of BRC4, Chetan Nayak, tweeted unfounded and disproven accusations that archive was leaked by MdSec and said they were the ones who uploaded it to VirusTotal. It is not known who uploaded the file.
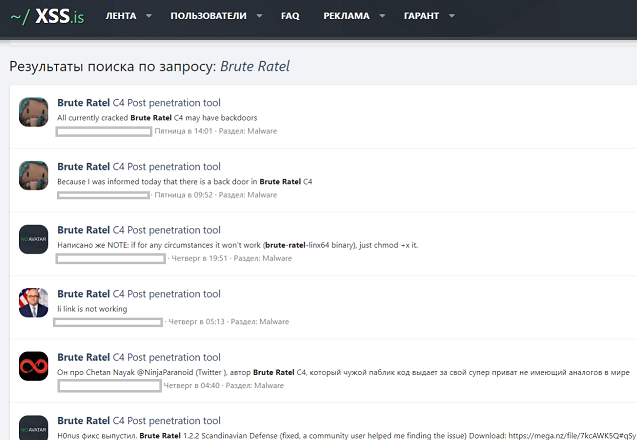
Nayak also stated a Russian-speaking group known as Molecules were the ones responsible for producing the cracked version of the product. This means that with the right instructions, the cracked tool can now be run without the activation key that is required to launch the full software and use its features.
There are now multiple posts on multiple of the most populated cybercrime forums where data brokers, malware developers, initial access brokers, and ransomware affiliates all hang out. This includes BreachForums, CryptBB, RAMP, Exploit[.]in, and Xss[.]is, as well as various Telegram and Discord groups. Threat actors connected to various organized cybercrime groups have expressed interest in the leak of the new tool.
So What?
In July 2022, Sophos incident responders encountered Brute Ratel in the wild, alongside Cobalt Strike, at an ALPHV (aka BlackCat) ransomware engagement. Therefore, we know cybercriminals, especially ransomware affiliates, are going to be using this tool in the short-to-medium term. The BRC4 leak has also come shortly after another significant leak in the cybercriminal underground, which involved the LockBit Ransomware-as-a-Service (RaaS) group. Rumours spread that the RaaS was hacked, and the builder for LockBit Black (aka LockBit 3.0) was stolen and leaked online. VX-Underground later told BleepingComputer that LockBitSupp clarified with them that the leak legit but was due to a “programmer employed by LockBit ransomware group,” quelling rumours that LockBit RaaS had been hacked.
One of the most concerning aspects of the BRC4 tool for many security experts is its ability to generate shellcode that is undetected by many EDR and AV products. This extended window of detection evasion can give threat actors enough time to establish initial access, begin lateral movement, and achieve persistence elsewhere. Due to its evasive generation of new payloads it renders stopping Brute Ratel by the traditional blocking of Indicators of Compromise (IOCs) inadequate. It is recommended that defenders use behaviour-based detection opportunities to thwart attacks, like the ones outlined in MdSec’s blog (see here).
Overall, enterprises and public sector organizations must recognize the imminent threat of the proliferation of this tool. Its capabilities closely align with the objectives of ransomware groups that are already highly active and looking for new windows of opportunity.