One Way Or Another: Initial Access Vectors
Artwork by @laelcillustrate
The aim of this blog is to highlight initial access techniques that you’ve potentially not heard of before. You're unlikely to find these in the Mitre ATT&CK framework and these are pretty unlikely to happen day-to-day, but they are perfectly valid for persistent attackers. How to implement detection for these techniques also depends on your threat model and who is trying to target you or your organisation.
Traditional initial access techniques for common threats such as Ransomware operators or Advanced Persistent Threat (APT) groups include phishing for credentials, malicious spam containing malware, obtaining RDP credentials via brute force or purchasing them from underground markets, and exploiting a vulnerability in a public-facing system. The techniques discussed in this blog, however, requires a bit more determination, opportunism, and lateral thinking.
>> I've added some "Bushido comments" offering my own opinion and around each scenario. The aim of these are so that analysts are not left unequipped and have some starting points if tasked to research these particular threats
The one with the Fish Tank
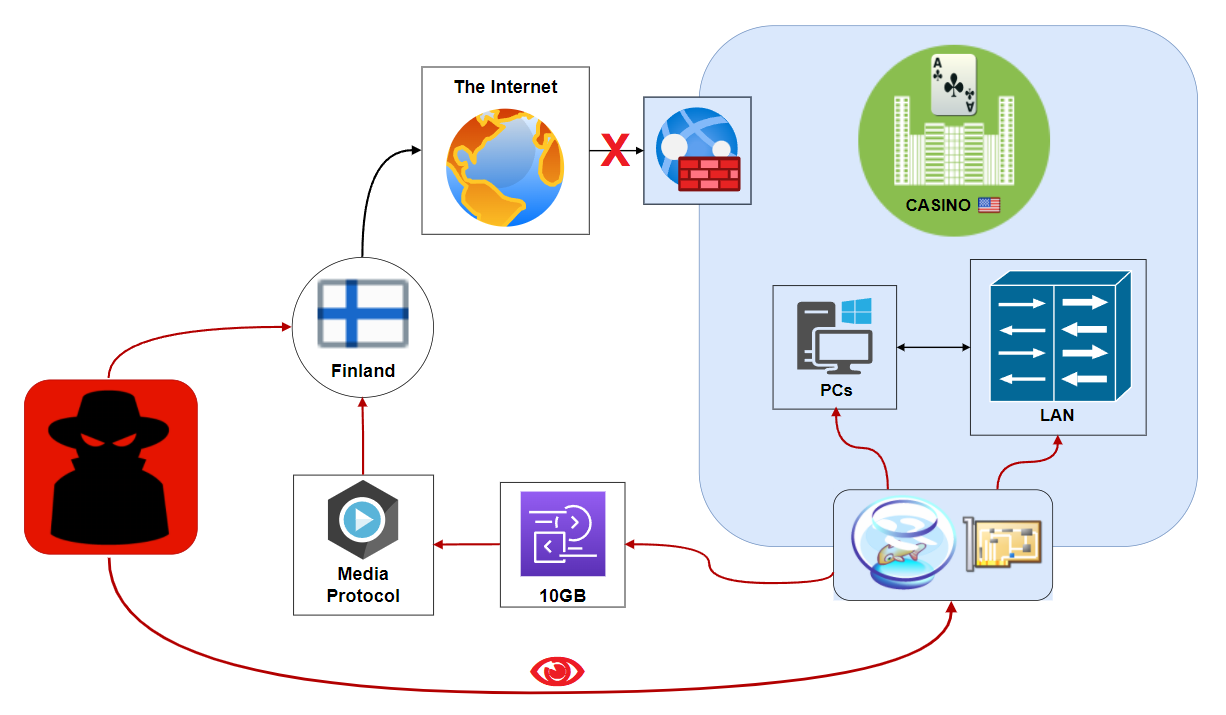
First up is a somewhat iconic report by none other than everyone's favourite "AI" cybersecurity firm, DarkTrace, whose 2017 Global Threat Landscape report detailed how a threat actor reportedly used an Internet-connected fish tank at a Casino. The threat actor (see Fig. 1 below) was seemingly unable to enter the company's network via traditional means (like the ones that were outlined above). Then, with a bit of fervour, they managed to uncover an anomalous device on the perimeter, one that the Infosec team had seemingly forgotten. This was all it took to establish an initial foothold, perform lateral movement, and exfiltrate sensitive data from the target environment undetected. (source)
Bushido comments:
- This highlights how keeping an inventory of your assets is key to stopping threat actors exploiting forgotten systems (also known as "Shadow IT"). It would be prudent to regularly track what, where, when, and why devices are connected to your organization
The one with the Personal Blog
Next, I chose to feature the tactics leveraged by a Russian cybercriminal called Yevgeniy Nikulin who was arrested in Prague in 2016 and was extradited to the US. He was the one who infamously broke into LinkedIn, as well as Dropbox and Formspring, and stole millions of records from each company. As impressive of a roster of victim Yevgeniy racked up, the way he compromised them is more fascinating.
He reportedly began by trawling LinkedIn for targets and found a software engineer he was going to go after (see Fig. 2 below). He then uncovered that the software engineer had a personal blog hosted on a residential IP address. Some further recon of the IP address uncovered it was a virtual machine on a personal iMac system. By exploiting a well-known vulnerability, Yevgeniy managed to gain initial access and compromised the virtual machine. What followed next was somewhat of a master stroke by an evil genius. Yevgeniy found that the virtual machine could connect locally to the iMac host through via SSH (Port 22). He then brute-forced his way to the host iMac machine, stole the valid VPN credentials from the software engineer, and connected to the LinkedIn corporate network and the rest was history. (source)
Bushido comments:
- The fun thing about this story is that the software engineer was probably never going to anticipate a threat actor trying this and might not have even realised it was a possibility
- Given that the software engineer worked at a high-profile company, they should have anticipated more persistent threat actors are likely to come after them
- When you work in a high position it is even more vital you should take every necessary step and precaution, lock down the basics as a minimum, and start thinking about or reviewing your threat model
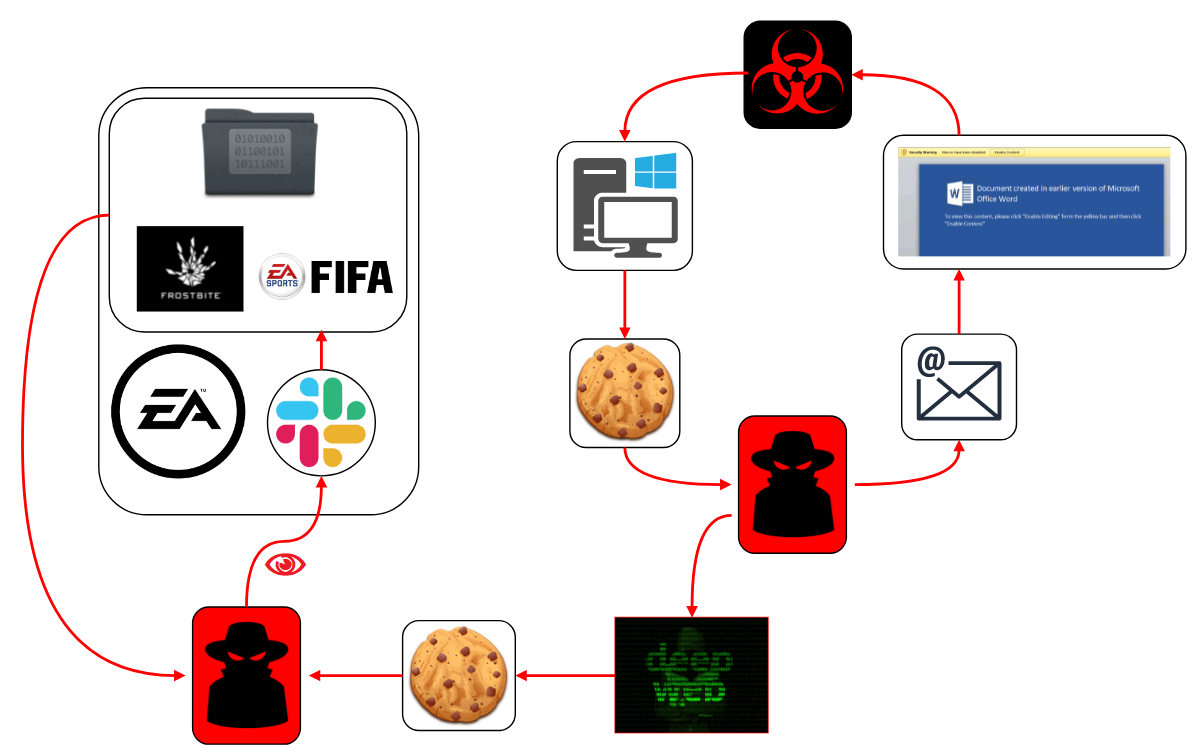
Electronic Arts (EA), voted one of America's worst companies (twice), had its source code stolen for its Frostbite engine and FIFA. All the technical details are unclear, but we do have a recount from one of the threat actors who allegedly assisted in the attack who shared details to VICE. The incident at EA most likely began with a malicious spam email containing a dodgy attachment. Someone with access to EA's Slack instance opened it and got infected with infostealing malware (such as Raccoon Stealer, Redline Stealer, AZORult, or Vidar Stealer) that collected and exfiltrate web browser credentials, web session cookies, and other authentication tokens (see Fig. 3 below). The cookie was then put up for sale on the long-running cybercriminal underground marketplace, Genesis Market. Several other markets do exist, however, such as Russian Market, 2EasyShop, Xleet, or Amigos (which recently closed).
A threat actor linked to the LAPSUS$ group reportedly later bought the cookie which gave then access to EA's Slack Channel. While logged in to a legitimate employee account, the threat actor contacted the IT helpdesk of EA and convinced them to provide access to code repositories, which was granted. This then led to Gigabytes of data being downloaded by the threat actor and subsequently used in an extortion attempt to get EA to pay for it not to be released publicly. EA did not pay (AFAIK) and the data was subsequently leaked to the cybercriminal underground. (source)
Bushido comments:
- Personally, I wouldn't blame the IT helpdesk in this scenario, the security systems already failed to stop the malware, remediate the device, and missed the anomalous login from an unrecognised system
- Cookie-stealing malware should not be ignored, infected systems need to be remediated and accounts need to be reset, browser caches should also be cleared
The one with the Android Emulator
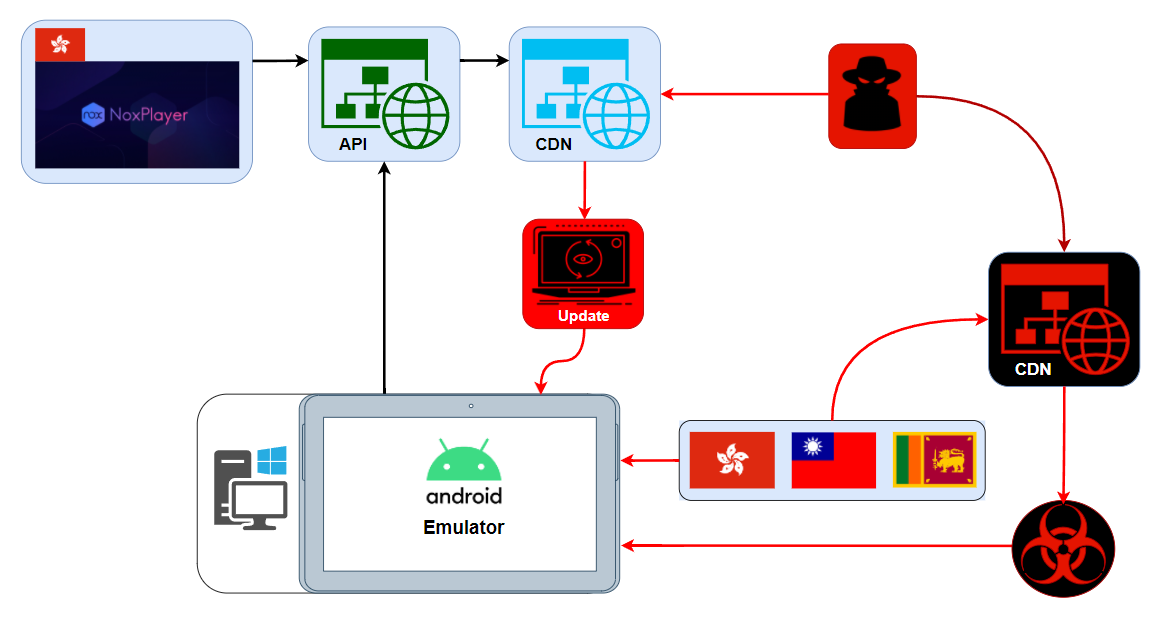
In March 2021, ESET researchers uncovered a software supply chain attack against emulation software, NoxPlayer, to install surveillance malware on the computers of online gamers (see Fig.4 below). The adversary targeted select users of NoxPlayer, a software package that emulates the Android operating system on PCs and Macs. People use it primarily for playing mobile Android games on these platforms. NoxPlayer-maker BigNox says the software has 150 million users in 150 countries. The infrastructure belonging to software developer, BigNox, was reportedly compromised by a sophisticated and potentially state-aligned adversary to push a malicious update. And, in some cases, additional payloads were downloaded by the BigNox updater from attacker-controlled servers. Notably, however, unlike the infamous SolarWinds supply chain attack, the malicious files were not digitally signed the way legitimate updates are, which suggests the BigNox software build system was not compromised; only the systems for delivering updates were. (source)
Bushido comments:
- Detecting supply chain compromise in general is very difficult, you don't generally anticipate that the vendors of the software you use will get popped one day to serve malicious updates - this has slightly changed though since SolarWinds happened
- To mitigate supply chain attacks you can turn off automatic updates and wait for verification from others it is safe to apply, use sandboxed devices, segment networks, use virtual machines, browser emulation, or even potentially a separate device on a VLAN - this all depends on your threat model in reality
The one with the USB
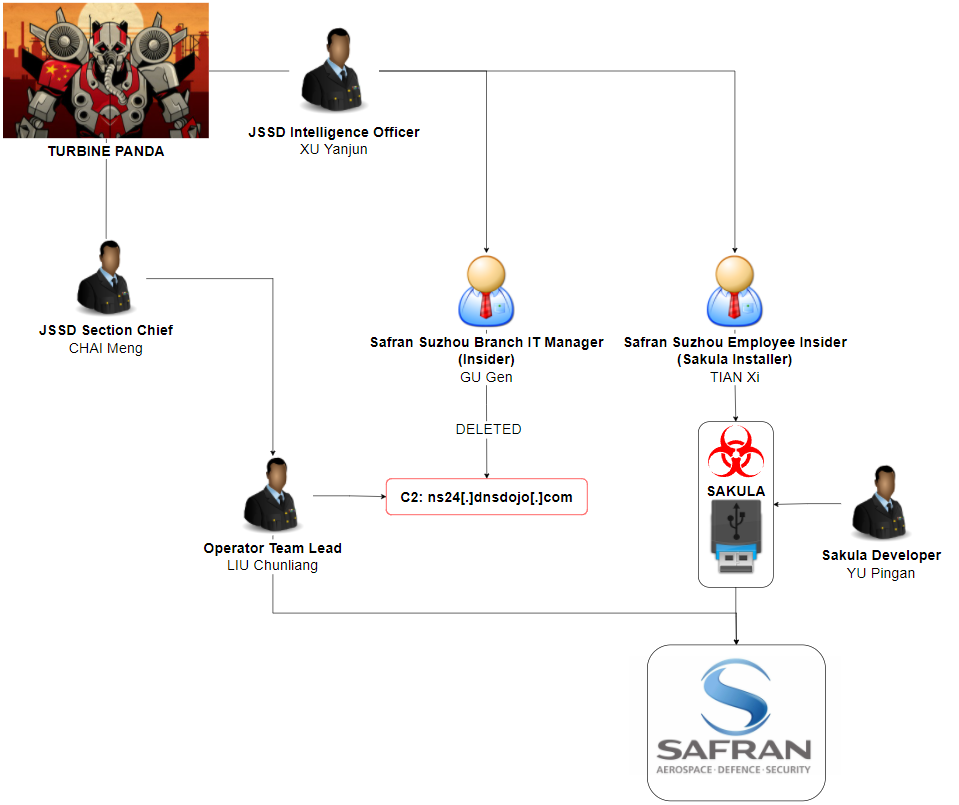
In October 2019, CrowdStrike released a report titled 'HUGE FAN OF YOUR WORK', which described in great detail about how the Chinese intelligence services launched a widespread intellectual property theft campaign targeting the aviation industry. CrowdStrike assesses that the campaign, dubbed TurbinePanda, aimed to "fill key technology and intelligence gaps" to enable its narrow-body twinjet airliner, the C919, to "compete against western aerospace firms". The campaign (see Fig. 5 below) hinged on having IT personnel stationed inside the targeted aviation industry organizations. The individual had physical access to systems with sensitive information on it. They were passed a malicious USB device, containing the Sakula malware, to insert into an enterprise system. Once connected, the TurbinePanda operators then had access to the victim's network and could then begin to siphon off critical proprietary information. To further conceal these actions, TurbinePanda also had access to an IT manager inside the target organization who could clear event logs and make the connections look like they never happened. (source)
Bushido comments:
- As noted by CrowdStrike analysts, rarely in this industry do cyber investigators get the luxury of knowing the full scope of their adversary’s campaign (from tasking, to actual operations, all the way to completion)
- The series of US Department of Justice (DoJ) indictments released over the course of two years, combined with CrowdStrike Intelligence’s own research, has allowed for startling visibility into a facet of China’s shadowy intelligence apparatus
- The group behind the TurbinePanda campaign was experienced, having also been tied to MSS Jiangsu Bureau, the likely perpetrators of the infamous 2015 US Office of Personnel Management (OPM) breach
- This report ultimately highlights the critical dangers of being targeted by a state-aligned, well-resourced advanced persistent threat (APT) actor and demonstrates that your chances of stopping them is incredibly low
- Ultimately, an APT group may eventually land on your systems one day, it is their entire reason for employment; one recommendation is just to invest more in security than your competitors and hope the APT goes for them instead!
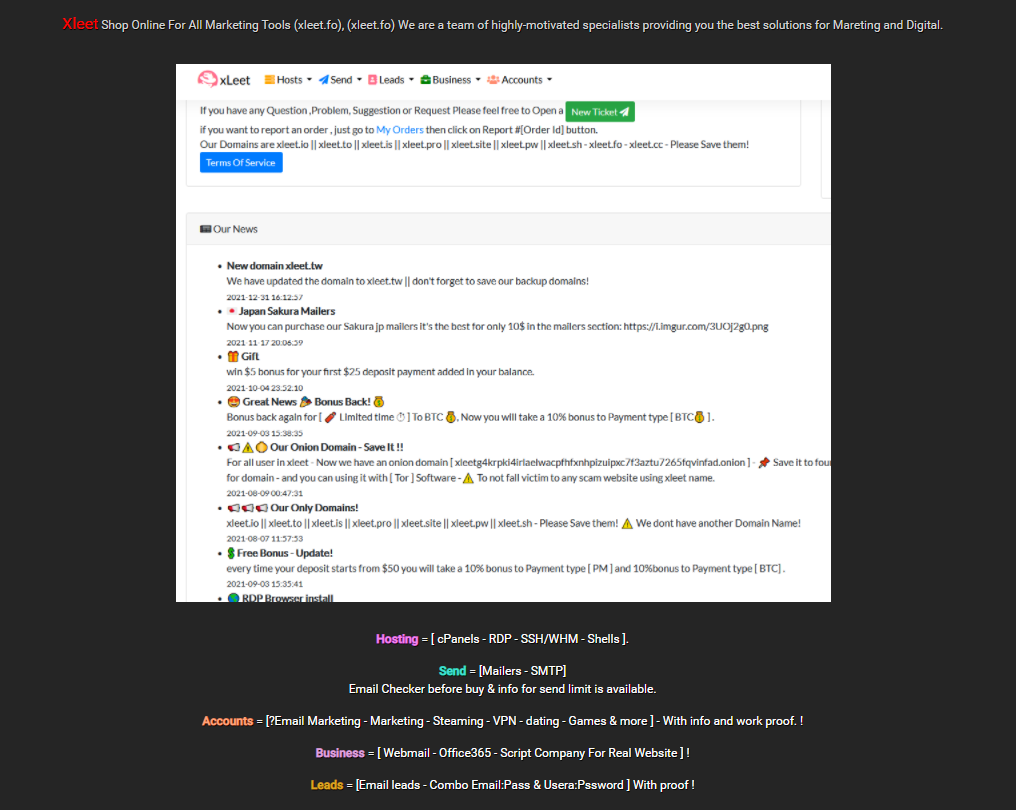
There is an entire underground economy that revolves around acquiring access to organizations just to sell it to other threat actors. One of the currently active marketplaces I decided to highlight in this blog is xLeet market (see Fig. 6 below). It is advertised on the Darkweb (which is really just Clearnet cybercrime forums) as a site where ultimately threat actors can buy access to compromised systems for use in any malicious activities they desire. Buyers can then pick and choose which organizations they want to compromise. The types of access ranges from shells, RDP credentials, email accounts, or website control panels. Establishing initial access themselves is no longer really required for threat actors, there's a good chance someone else has already done it and is happy to sell it on. (source)
Bushido comments:
- Monitoring access brokerages such as xLeet, Genesis, RussianMarket, 2EasyShop and others is not a simple task; the preferred way by most organization who are concerned about their exposure to these sites is via a threat intelligence team or vendor who can identify any mentions of the organization
- Considering the nature of cybercrime forums, the access offered on these brokerages is usually pretty low quality (and sometimes imaginary), if it was truly of value these cybercriminals wouldn't be selling it to others for as cheap as $5 to $10 a pop
Fig. 6 - xLeet access brokerage advertised on cybercrime forums
The Insider Threat
Insider threats is something many security teams at a variety of large organizations are becoming increasingly worried about. The current concern from insider threats revolves around the 'back-to-work' mandates, which could lead to a few disgruntled employees looking to take revenge after they have gotten used to working from home. In case you missed it, we are currently a 'ransomware golden age' with some groups earning millions (if not billions according to OFAC) of dollars through cyberattacks. This could well be quite the incentive for a financially motivated malicious insider.
In 2021, I was honoured to have my research featured in VICE for uncovering some additional websites (see Fig. 7 below) linked to a campaign looking to pay employees for their work credentials. It is unknown what 'Unite At Work' aimed to do with such credentials, but it sounded pretty dodgy and illegal to me. (source)
Setting up fake companies to recruit cybercriminals is not something new, the FIN7 group (linked to DarkSide and BlackMatter ransomware and responsible for the Colonial Pipeline incident) was known for doing just this across Eastern Europe to hire hackers to conduct ransomware operations. If your employees get contacted to work for "Combi Security" or "Bastion Secure", alarm bells should be ringing. (source)
Bushido comments:
- The insider threat is one of the final frontiers for the cybersecurity industry. It is a tough nut to crack. It may seem like it rarely happens, but this is most likely due to it going unreported and undetected.
- The hardest part about tackling the insider threat challenge is that it requires doing everything correctly, RBAC, TPAM, audits, "Zero Trust" - something that many organizations do not do fully or correctly
- For many that just have no hope of stopping a privileged malicious insider, we basically have to hope they realize through deterrence that the consequences of the getting caught are not worth the criminal rewards
Theoretical attacks?
If you think some of the techniques described above are easy to detect and prevent, I invite you to try reading up on some of the mind-bending research from Israel's Ben Gurion University:
- Data exfiltration via sending info over PCs' power supply cables (source)
- Smartphone hackers can glean secrets by analysing touchscreen user interactions (source)
- AIR-FI: Generating Covert Wi-Fi Signals from Air-Gapped Computers (source)
- LAN cables' radio frequency emissions can be read by using a $30 off-the-shelf setup (source)
Courses of Action
- The aim of this blog is to shed light on how threat actors can use a plethora of techniques to infiltrate your network and can get very creative when phishing or pwning unpatched systems at the edge doesn't work
- It is recommended to regularly perform Gap Analysis of your organization's visibility and prioritization resources to close them (which should be based on risk score)
- Do the basics: use 2FA/MFA, use password managers, patch edge systems
- Think about how trusted relationships could be exploited (e.g. exclusion lists/whitelisted processes) and supply chain risks (e.g. partners/vendors that have been breached)
- Many organizations only keep logs for two weeks to one month, maybe up to 90 days, if a threat actor can go undetected for that long they are much less likely to be uncovered and removed - we should anticipate that adversaries may already be inside the network and should use threat hunting methodologies to uncover suspicious activities