Tracking A Renewable Energy Intelligence Gathering Campaign
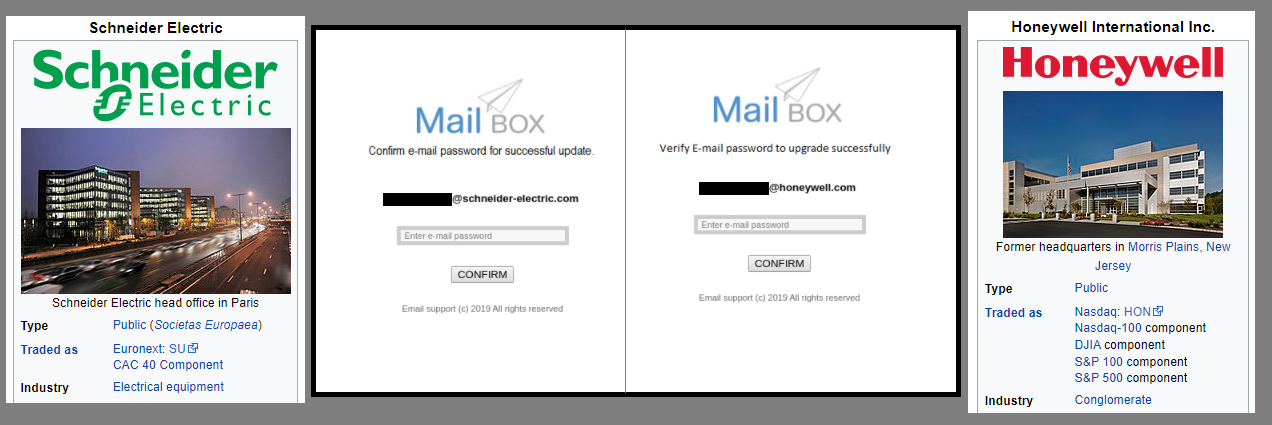
For my first research blog of 2022, I analysed a suspected intelligence gathering campaign targeting renewable energy and industrial technology organisations, with a particular focus on Bulgaria. This long-running espionage campaign leveraged multiple credential harvesting pages to target the email accounts of employees at a number of organisations between 2019 and is ongoing in 2022. The attackers use the same 'Mail Box' phishing kit and host many of the pages on them infrastructure, supported by also compromising some legitimate websites.
This research was conducted using OSINT techniques such as query public sandbox submissions and passive DNS scan results. From this up to 40 individuals at target organisations from a variety of sectors were identified, but there was a focus on a few such as renewable energy, environmental protection organisations, and industrial technology. This research using OSINT alone is unable to acquire the full story, but hopefully can paint a picture of the motivation of the adversary behind this campaign.
Some of the targets include high-profile organisations such as operational technology (OT) and industrial control system (ICS) vendors like Schneider Electric and Honeywell, as well as Chinese telecommunications giant Huawei, semiconductor manufacturer HiSilicon, Telekom Romania, and US universities such as the University of Wisconsin, California State University, and Utah State University.
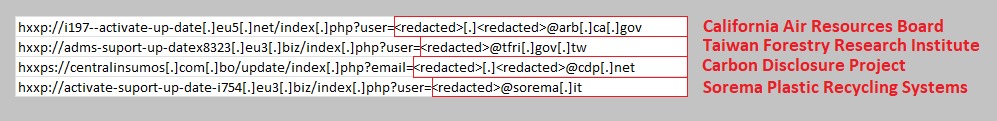
As mentioned above, one of the focuses of the campaign appeared to be renewable energy and environmental protection organisations. This includes the Kardzhali Hydroelectric Power Station (vec[.]nek[.]bg) and CEZ Electro (cez[.]bg), both located in Bulgaria, as well as the California Air Resources Board (arb[.]ca[.]gov), Morris County Municipal Utilities Authority (mcmua[.]com), the Taiwan Forestry Research Institute (tfri[.]gov[.]tw), the Carbon Disclosure Program (cdp[.]net), and Sorema, an Italian plastic recycling firm. There was also a small cluster of activty in 2019 linked to the same infrastructure targeting multiple banks in Bulgaria too.
Analysis
Attribution
| Type | Indicator | Context |
| Hostname | activate-suport-up-date-142i[.]eu5[.]net | Hosts 'Mail Box' phishing kit |
| Hostname | adm-up-da-te-x2020x89354[.]eu5[.]net | Hosts 'Mail Box' phishing kit |
| Hostname | i197--activate-up-date[.]eu5[.]net | Hosts 'Mail Box' phishing kit |
| Hostname | xt543-suport-up-date[.]eu5[.]net | Hosts 'Mail Box' phishing kit |
| Hostname | 8xe3615-12-2019-up-date[.]eu3[.]org | Hosts 'Mail Box' phishing kit |
| Hostname | i131dere-up-date[.]eu3[.]biz | Hosts 'Mail Box' phishing kit |
| Hostname | jan-6543-up-date[.]eu3[.]biz | Hosts 'Mail Box' phishing kit |
| Hostname | x437-suport-up-dates[.]eu5[.]net | Hosts 'Mail Box' phishing kit |
| Hostname | e541-suport-up-date[.]eu5[.]net | Hosts 'Mail Box' phishing kit |
| Hostname | x914-suport-up-date[.]eu5[.]net | Hosts 'Mail Box' phishing kit |
| Hostname | 4877-activate-up-date[.]eu5[.]net | Hosts 'Mail Box' phishing kit |
| Hostname | active-up-date-xk89si[.]eu5[.]net | Hosts 'Mail Box' phishing kit |
| Hostname | activate-suport-up-date-i754[.]eu3[.]biz | Hosts 'Mail Box' phishing kit |
| Hostname | activate-suport-up-date-i754[.]eu3[.]biz | Hosts 'Mail Box' phishing kit |
| Hostname | activate-suport-up-date-321i[.]eu3[.]biz | Hosts 'Mail Box' phishing kit |
| Hostname | adms-suport-up-datex8323[.]eu3[.]biz | Hosts 'Mail Box' phishing kit |
| Hostname | 05-2019-up-date[.]eu5[.]net | Hosts 'Mail Box' phishing kit |
| Hostname | x07-2019-up-date[.]eu5[.]net | Hosts 'Mail Box' phishing kit |
| Hostname | 08-2019-up-datex[.]eu5[.]net | Hosts 'Mail Box' phishing kit |
| Hostname | 07-2019-up-datex[.]eu5[.]net | Hosts 'Mail Box' phishing kit |
| Hostname | adms-up-date-2020[.]eu5[.]net | Hosts 'Mail Box' phishing kit |
| Hostname | adm-up-date-2020x68293[.]eu5[.]net | Hosts 'Mail Box' phishing kit |
| Hostname | 08-2019-up-da-tex[.]eu5[.]net | Hosts 'Mail Box' phishing kit |
| Hostname | 06-2019-up-date1[.]eu5[.]net | Hosts 'Mail Box' phishing kit |
| Hostname | 04-2019-upd[.]eu5[.]net | Hosts 'Mail Box' phishing kit |
| IPv4 | 185[.]176[.]43[.]106 | Hosts *.eu3[.]biz *.eu3[.]org *.eu5[.]net pages |
| IPv4 | 185[.]176[.]43[.]90 | Hosts *.eu3[.]biz *.eu3[.]org *.eu5[.]net pages |
| IPv4 | 185[.]176[.]43[.]98 | Hosts *.eu3[.]biz *.eu3[.]org *.eu5[.]net pages |
| IPv4 | 185[.]176[.]43[.]96 | Hosts *.eu3[.]biz *.eu3[.]org *.eu5[.]net pages |
| IPv4 | 185[.]176[.]43[.]94 | Hosts *.eu3[.]biz *.eu3[.]org *.eu5[.]net pages |
| IPv4 | 185[.]176[.]43[.]80 | Hosts *.eu3[.]biz *.eu3[.]org *.eu5[.]net pages |
| IPv4 | 185[.]176[.]43[.]84 | Hosts *.eu3[.]biz *.eu3[.]org *.eu5[.]net pages |
| IPv4 | 185[.]176[.]43[.]82 | Hosts *.eu3[.]biz *.eu3[.]org *.eu5[.]net pages |
| IPv4 | 185[.]176[.]43[.]80 | Hosts *.eu3[.]biz *.eu3[.]org *.eu5[.]net pages |
| URL | hxxp://saleswarriorinc[.]com/aba/login/index[.]php | Compromised website to host 'Mail Box' phishing kit |
| URL | hxxp://armaghanteb[.]com/bul/login/index[.]php | Compromised website to host 'Mail Box' phishing kit |
| URL | hxxp://quadteximagery[.]com/veri/login/index[.]php | Compromised website to host 'Mail Box' phishing kit |
| URL | hxxps://primage[.]com[.]br/aa/update/index[.]php | Compromised website to host 'Mail Box' phishing kit |
| URL | hxxps://alphabitconsulting[.]com/veri/login/index[.]php | Compromised website to host 'Mail Box' phishing kit |
| URL | hxxps://centralinsumos[.]com[.]bo/update/index[.]php | Compromised website to host 'Mail Box' phishing kit |
| URL | hxxps://pwametalurgica[.]com[.]br/bb/update/index[.]php | Compromised website to host 'Mail Box' phishing kit |
| URL | hxxps://cercoselectricos[.]cl/aa/update/index[.]php | Compromised website to host 'Mail Box' phishing kit |
| URL | hxxps://flammaautomoveis[.]com[.]br/bul/update/index[.]php | Compromised website to host 'Mail Box' phishing kit |
| URL | hxxp://englishlessons-houston[.]com/les/welcome/?user= | Compromised website to host 'Mail Box' phishing kit |
| URL | hxxp://saojoaodaurtigars[.]com[.]br/malaysia/login/?user= | Compromised website to host 'Mail Box' phishing kit |