Analysis of the latest PayPal phishing attacks
As far as brands that get impersonated a lot, PayPal has got to be in the Top 5 or Top 3 globally. Between August and October, I personally received 19 PayPal credential phishing page links and my crud email provider (not Gmail or Outlook) didn't block them, so they've been landing in my inbox. So I took a look at them, natch. I examined various phishing attempts that appear to be sent in a similar manner to my personal email, which has only appeared in one small breach in 2017, according to Have I Been Pwned for the record.
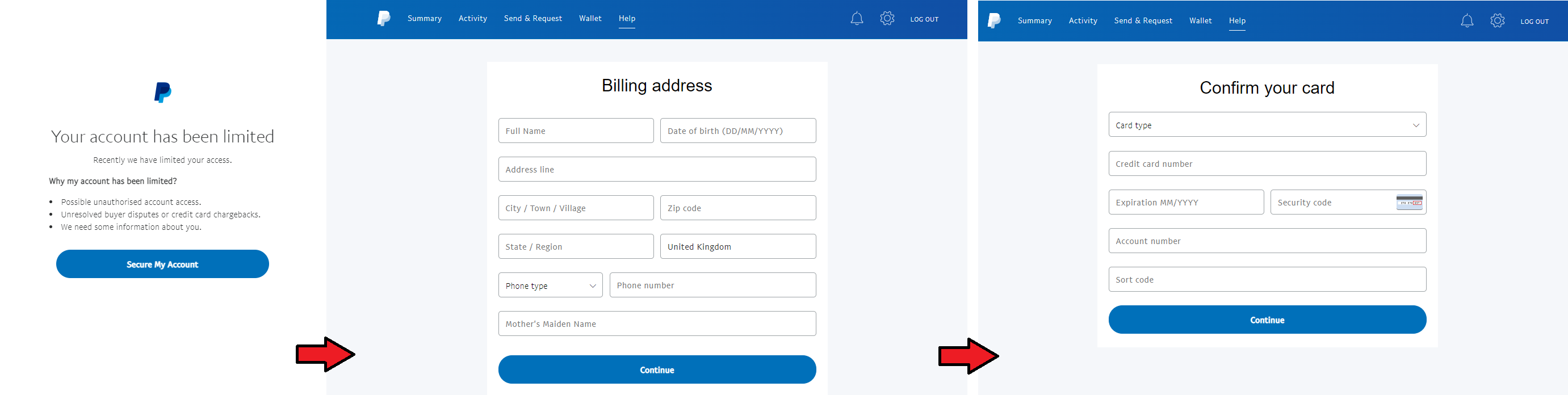
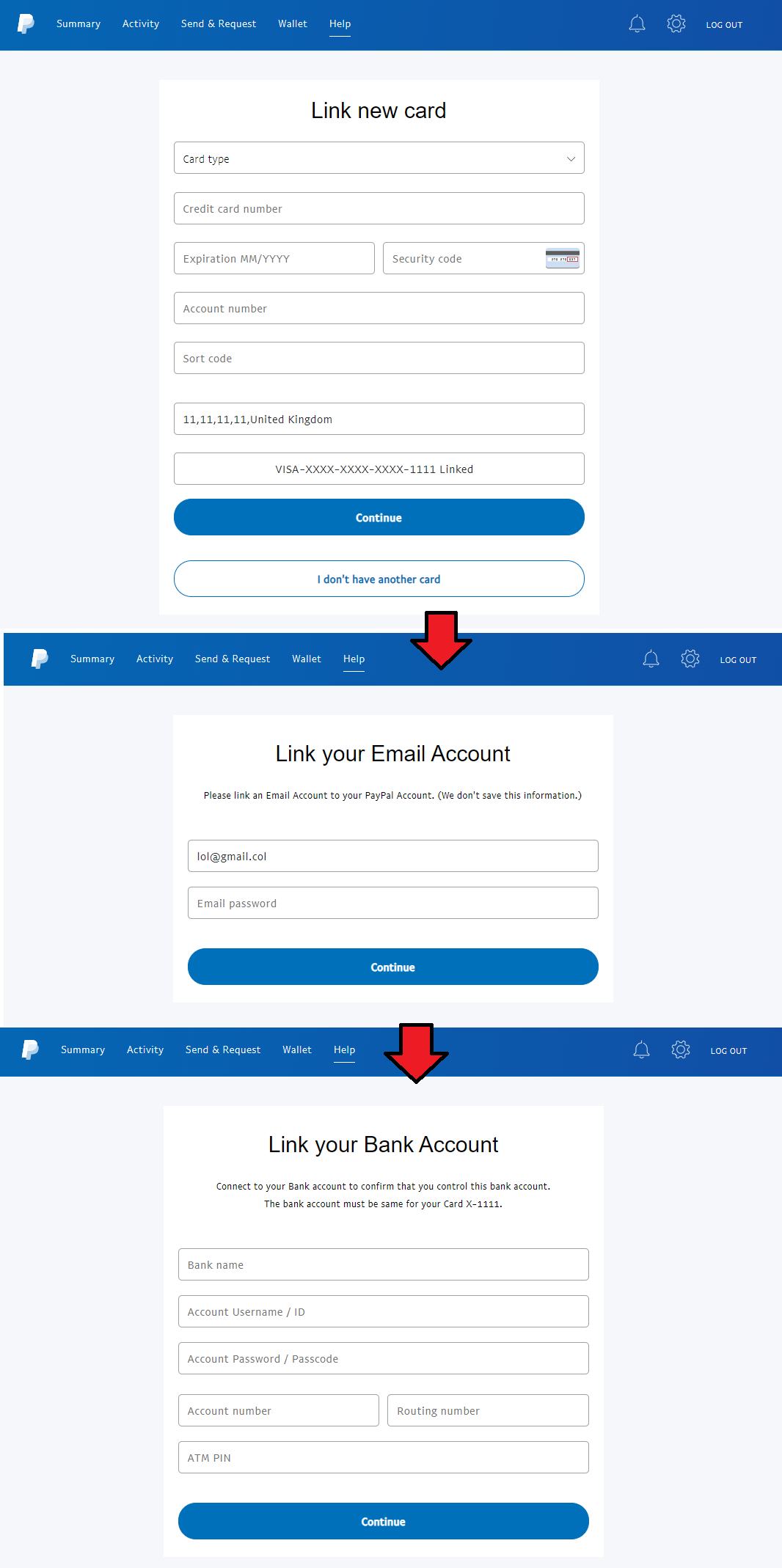
One phishing kit stood out and forced my hand into blogging about it. It consisted of 11 parts, including the phishing email itself and the initial landing page; followed by several pages to harvest credit card and billing information, bank account details, and finally the bit that I'd not personally seen before (but I doubt is that new) was that it asked me to "Upload your identity".
Interestingly, this PayPal phishing email leverages an Open Redirect in WhatsApp shortened URL:
Try it yourself, you can add any URL after the "https://l.wl.co/l?u=" part of the link - even a PayPal phishing page:
Might want to fix that, WhatsApp
Indicators of Compromise (IOCs):
Sender Email:
ckul31gcijzl9ev-ql3keowlfcjlnliy[@]emaildl.att-mail[.]com
Redirect URL:
hxxps://l[.]wl[.]co/l?u=hxxps://qr[.]paps[.]jp/XvICB?userid=LIYnPBFM
Phishing pages:
hxxps://teamputugamingalwayson[.]chickenkiller[.]com/security/alert/file/myaccount?key=<redacted>
hxxps://teamputugamingalwayson[.]chickenkiller[.]com/security/alert/file/myaccount/unusual?key=<redacted>
hxxps://teamputugamingalwayson[.]chickenkiller[.]com/security/alert/file/myaccount/account?key=<redacted>
hxxps://teamputugamingalwayson[.]chickenkiller[.]com/security/alert/file/myaccount/card?key=<redacted>
hxxps://teamputugamingalwayson[.]chickenkiller[.]com/security/alert/file/myaccount/link_card?key=<redacted>
hxxps://teamputugamingalwayson[.]chickenkiller[.]com/security/alert/file/myaccount/link_email?key=<redacted>
hxxps://teamputugamingalwayson[.]chickenkiller[.]com/security/alert/file/myaccount/bank?key=<redacted>
hxxps://teamputugamingalwayson[.]chickenkiller[.]com/security/alert/file/myaccount/identity?key=<redacted>