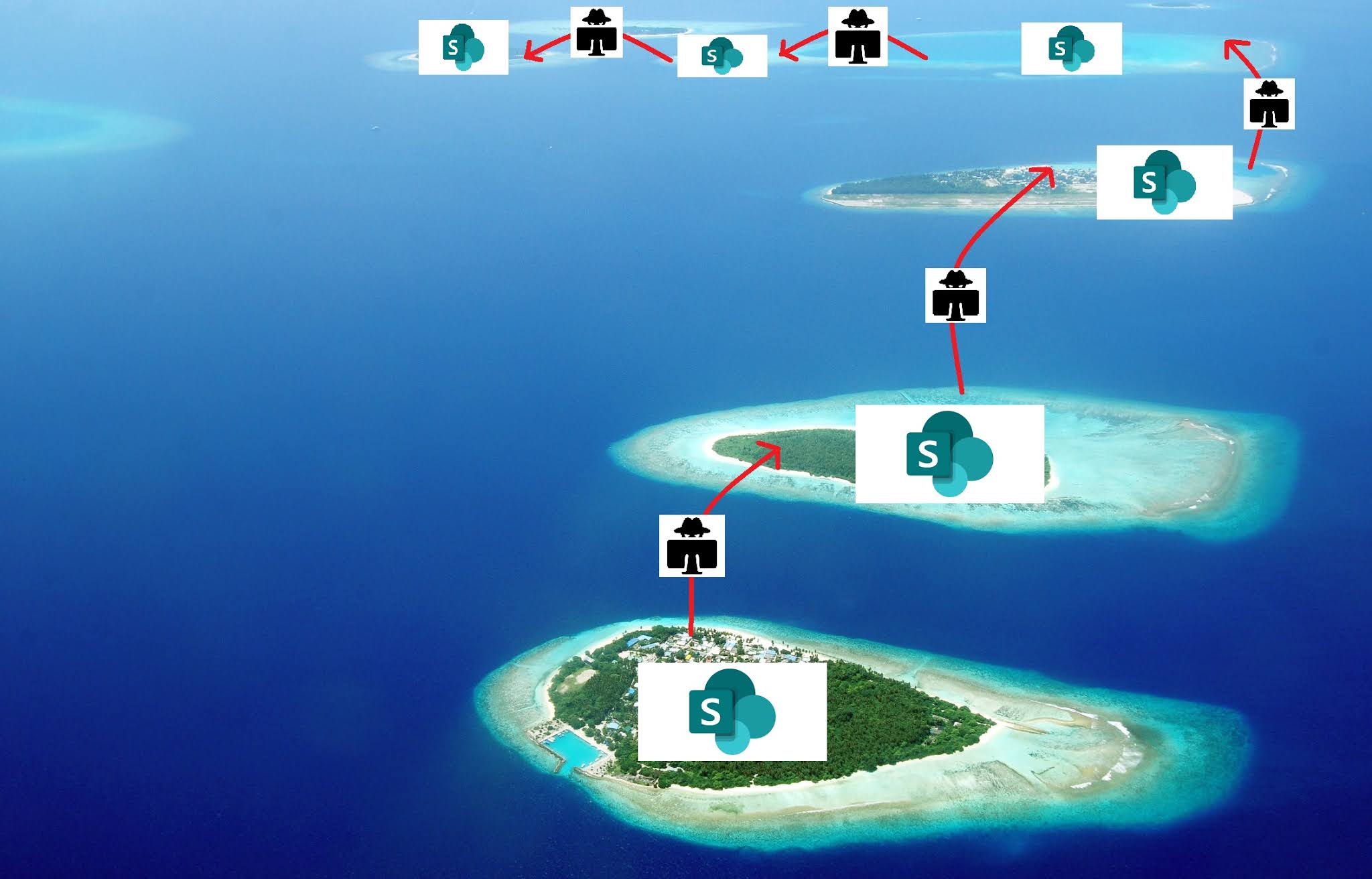
SharePoint Island Hopping: Phishing with compromised accounts
Phishing threat actors continue to launch successful credential harvesting campaigns via compromised Office 365 accounts. One of the most common themes for these campaigns is a "shared file" notification, whereby a compromised account shares a file with a user that is hosted in the SharePoint drive. The file is usually a PDF document that contains a URL to an external site embedded in an "open document" or "view file" button. If the user clicks on it and enters their credentials they are redirected to login.microsoftonline.com.
Although this is an older scam, that has been around for several years, it is still highly effective and is being used to leap from one organisation to another. In this blog, I will analyse a long running phishing campaign that has compromised at least 45 different SharePoint accounts belonging to a variety of organisations over the last year.
Attributes of this phishing campaign which largely remained the same each time:
- The phishing email is a "shared file" notification sent by the compromised account
- The attackers use a PDF hosted on SharePoint with an embedded URL
- The URL would point to a *.hostingerapp[.]com hostname with the fake OneDrive login page
- Two files called 1.html and next.php collect the credentials and redirect the user
- Users are redirected to login.microsoftonline.com if they enter credentials
Further investigation into the campaign revealed other variations of the attack, which still uses the core attributes such as PDFs with embedded URLs and the same OneDrive phishing kits on *.hostingerapp[.]com hostnames.
Analysis:
There is a variety of organisations impacted by this campaign, as seen in the IOCs section below. This includes US schools and colleges, engineering firms, professional services, logistics firms, and manufacturers, among others. This seemingly random variety indicates it is an opportunistic spam campaign rather than targeted spear-phishing attacks. However, acquiring access to a large number of Office 365 accounts at various organisations could lead to targeted follow on attacks and subsequent malware or business email compromise (BEC) incidents. We often see threat actors create auto-forwarding rules on these accounts that monitor for keywords such as "invoice", "ACH", "RFQ", "payment", "order", and so on. The forwarded emails are then reviewed and the threat actors can follow up with a fake "invoice" or "update ACH" email posing as one of the organisation's partners.
By using *.hostingerapp[.]com hostnames the threat actors are able to hijack any pre-established trust associated with a given service's IP addresses and domains. These legitimate services are often abuse by cybercriminals to evade detection and slip past secure email gateways (SEG) and intrusion detection systems (IDS). This campaign uses several steps to evade detection systems, chiefly the use of hijacked SharePoint accounts and shared file notications to distribute the phishing documents. There is very little variation in these attacks during the entire year-long campaign, which goes to show it is a tried and tested, reliable technique for these cybercriminals to successfully harvest credentials.
Defenders should consider blocking or reviewing *.hostingerapp[.]com hostnames. Not only is it used in this long-running phishing campaign but also by a variety of malware families in 2018/19, such as AZORult, Imminent RAT, NanoCore RAT, and the Megalodon Stealer. [1, 2, 3, 4]
All organisations need to avoid becoming part of these campaigns. This includes enforcing multi-factor authentication (MFA), enforcing a timely password reset policy for all Office 365 accounts, removing accounts of employees who have left the organisations, and monitor for the creation of any email forwarding rules. It may also be worth monitoring for IP addresses and devices of the users logging into their Office 365 accounts. If a user who usually logs in via Google Chrome from the US or UK everyday suddenly logs in from Russia or Nigeria via Firefox it is worth investigating.
References:
- https://twitter.com/James_inthe_box/status/1069611890802778112?s=20
- https://twitter.com/KorbenD_Intel/status/1163929665230299137?s=20
- https://twitter.com/p5yb34m/status/1167130345965117440?s=20
- https://twitter.com/James_inthe_box/status/1075766442849533952?s=20
Indicators of Compromise (IOCs):
Malicious *.hostingerapp[.]com hostnames:
- 09jsl8-msd9smdi-29ims[.]hostingerapp[.]com
- brait3rm-pr0slamdoc8r[.]hostingerapp[.]com
- crearny-piesugat[.]hostingerapp[.]com
- dreamlessdocb-offlinprodoc[.]hostingerapp[.]com
- ericbrown-scudoc[.]hostingerapp[.]com
- evelyndocument-lastingsecur7[.]hostingerapp[.]com
- gr8testb1coin-84mfh40pro[.]hostingerapp[.]com
- homy-preparations[.]hostingerapp[.]com
- kristaz-doguments[.]hostingerapp[.]com
- lencrpted-trumetmsg[.]hostingerapp[.]com
- lifedoubledoc-sharepr0m[.]hostingerapp[.]com
- lightening-securesolo[.]hostingerapp[.]com
- mymovez[.]hostingerapp[.]com
- pr0spertie54-quadr9pop[.]hostingerapp[.]com
- prestige-onedr1ve-docc[.]hostingerapp[.]com
- prirmary-mgcheck[.]hostingerapp[.]com
- sleh94manne3-oxt93m049[.]hostingerapp[.]com
- smallows3r-smallows3r[.]hostingerapp[.]com
- sparow-sparow24[.]hostingerapp[.]com
- special707-o49mdpr0[.]hostingerapp[.]com
- speeedie24hs-documents365[.]hostingerapp[.]com
- torexserv-pieblokdoc[.]hostingerapp[.]com
- trptap-mytprojatv[.]hostingerapp[.]com
- worldrm-fintechz[.]hostingerapp[.]com
- mycentenary-my[.]sharepoint[.]com
- dmscan-my[.]sharepoint[.]com
- hsincorporated-my[.]sharepoint[.]com
- katherinefrank-my[.]sharepoint[.]com
- vivexbiomedical-my[.]sharepoint[.]com
- universaltechnologies-my[.]sharepoint[.]com
- amwarelogistics-my[.]sharepoint[.]com
- collierschools-my[.]sharepoint[.]com
- mteck-my[.]sharepoint[.]com
- hdceicom-my[.]sharepoint[.]com
- mapitgo-my[.]sharepoint[.]com
- nitcoinc-my[.]sharepoint[.]com
- blackbeltinsurors-my[.]sharepoint[.]com
- tmxno-my[.]sharepoint[.]com
- pyrongroup-my[.]sharepoint[.]com
- evolutioninsurecom-my[.]sharepoint[.]com
- groceryoutletinc-my[.]sharepoint[.]com
- covga-my[.]sharepoint[.]com
- metrojacksonobgyn-my[.]sharepoint[.]com
- bbmkbtr-my[.]sharepoint[.]com
- mpcyak-my[.]sharepoint[.]com
- groceryoutletinc-my[.]sharepoint[.]com
- mstfdonor-my[.]sharepoint[.]com
- h2otreat-my[.]sharepoint[.]com
- tamakilaw-my[.]sharepoint[.]com
- azliver-my[.]sharepoint[.]com
- doddburnham-my[.]sharepoint[.]com
- phgllc-my[.]sharepoint[.]com
- dnaz-my[.]sharepoint[.]com
- ericryan-my[.]sharepoint[.]com
- mortgagemasters-my[.]sharepoint[.]com
- broadbandhospitality-my[.]sharepoint[.]com
- regionallandtitle-my[.]sharepoint[.]com
- regionaltitleservices-my[.]sharepoint[.]com
- pawpawtownship-my[.]sharepoint[.]com
- inopo-my[.]sharepoint[.]com
- enterprisesinc-my[.]sharepoint[.]com
- whittyengineering478-my[.]sharepoint[.]com
- eeiengineers-my[.]sharepoint[.]com
- netorg5047480-my[.]sharepoint[.]com
- matx-my[.]sharepoint[.]com
- priority1inc-my[.]sharepoint[.]com
- westgatemfg-my[.]sharepoint[.]com
- shawlundquist-my[.]sharepoint[.]com
- metrojacksonobgyn-my[.]sharepoint[.]com