SharePoint Island Hopping: Phishing with compromised accounts
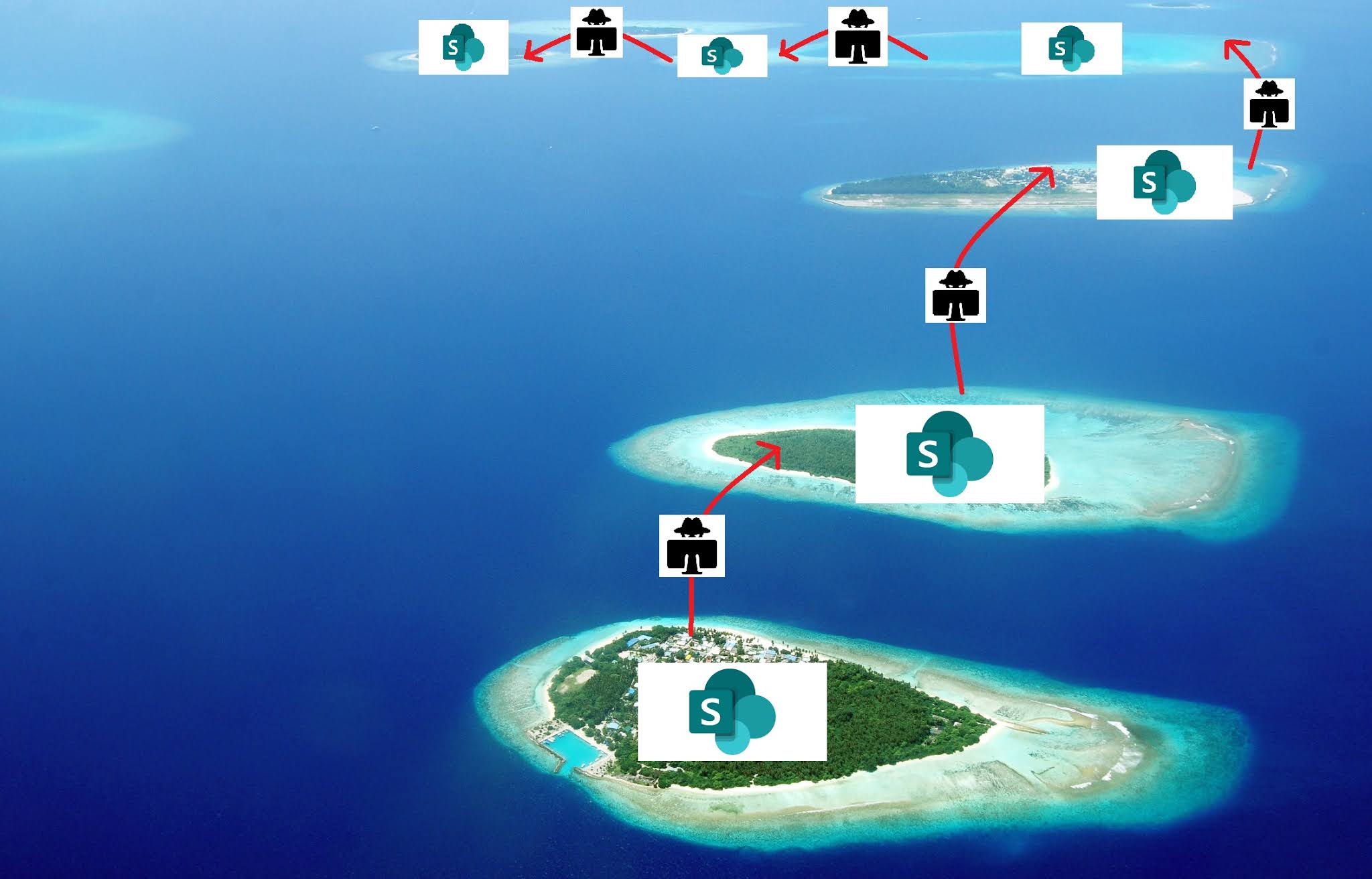
Phishing threat actors continue to launch successful credential harvesting campaigns via compromised Office 365 accounts. One of the most common themes for these campaigns is a "shared file" notification, whereby a compromised account shares a file with a user that is hosted in the SharePoint drive. The file is usually a PDF document that contains a URL to an external site embedded in an "open document" or "view file" button. If the user clicks on it and enters their credentials they are redirected to login.microsoftonline.com. Although this is an older scam, that has been around for several years, it is still highly effective and is being used to leap from one organisation to another. In this blog, I will analyse a long running phishing campaign that has compromised at least 45 different SharePoint accounts belonging to a variety of organisations over the last year. Fig. 1 - The typical phishing chain used in this campaign Fig. 2 - Various PDF documents...