Mobile Banking Phishing Campaign
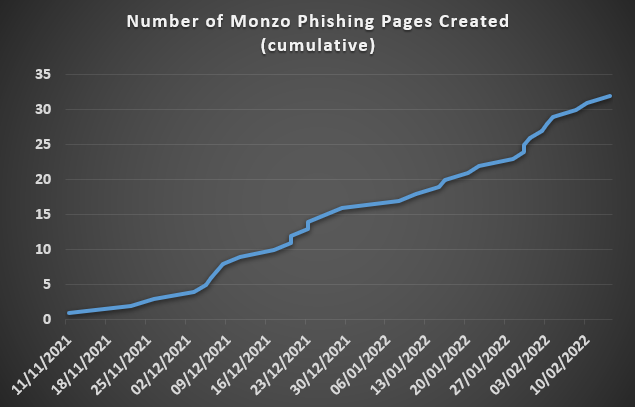
There is no doubt that mobile banking has taken the world by storm. Another growth industry is digital-only banks, especially in the UK. As of January 2022, over a quarter (27%) of British adults have opened an account with a digital-only bank, equating to 14 million people. This has created a new pool of targets for phishing threat actors to create new campaigns for fraud. This blog will explore a recent and ongoing campaign targeting mobile users and digital-only banks.
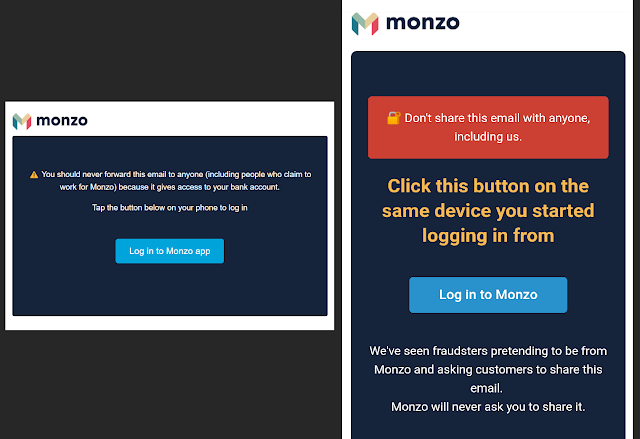
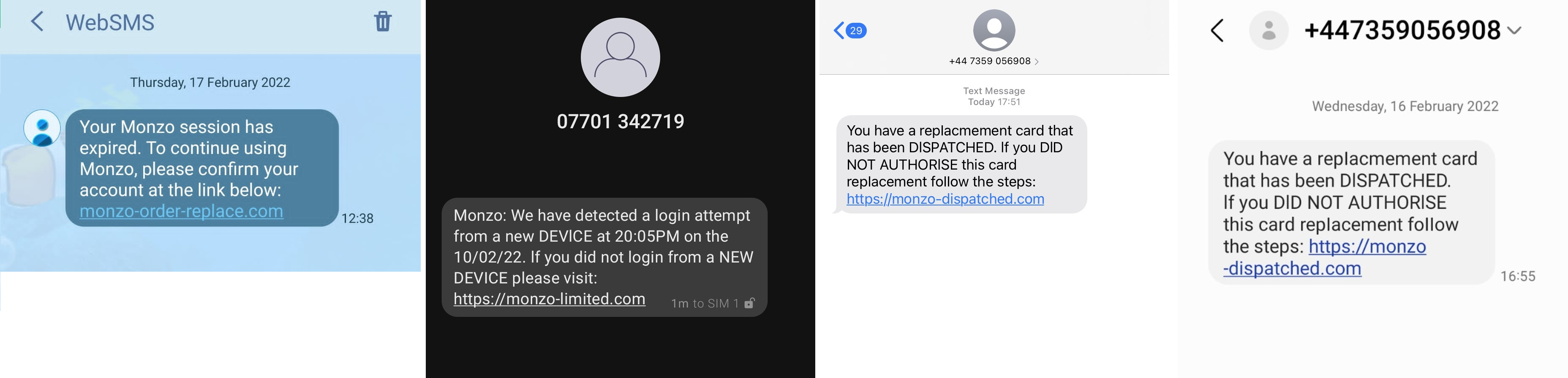
Monzo is a popular digital-only bank in the UK. For years, users are able to open an account without having to visit a branch just by walking through the steps in the mobile application. One of the key parts to creating a Monzo account is verifying your device. Monzo will send you a "golden link" which you use to login to for the first time (see Fig. 1). This is what the phishing threat actors are after.
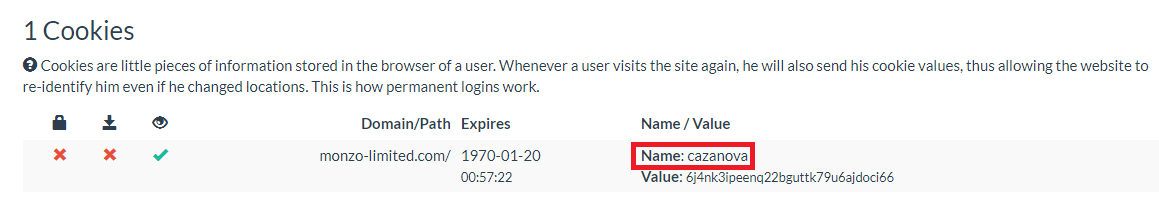
Analysis of the phishing kits deployed on these sites themselves revealed links to the Cazanova Morphine kit, detailed by the good people at WMC Global here. You don't have to look too hard to find Cazanova's fingerprints all over this kit (see Fig. 5).
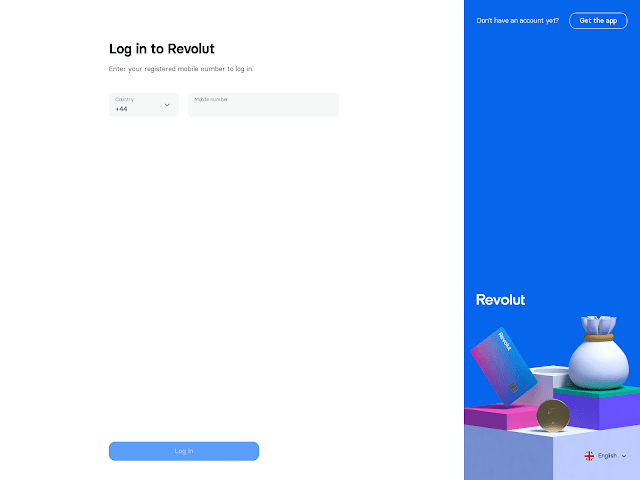
Digging some more into the ASN on URLscan.io uncovered some additional Revolut-themed phishing pages, again targeting mobile digital-only banking customers (see Fig. 6). Analysis of the domain registrar also revealed the use of NiceNic again, same as the Monzo phish and indicating it is likely the same phisher behind both campaigns.
Indicators of Compromise
- monzo-card-alerts[.]com
- monzo-support-online[.]com
- monzo-check[.]com
- monzo-card-support[.]com
- monzo-review-account[.]com
- monzo-cancel-online[.]com
- monzo-support-review[.]com
- monzo-cancel[.]com
- monzo-cancel-card[.]com
- alert-monzo[.]com
- monzo-online-support[.]com
- monzo-reviews[.]com
- monzo-address-uk[.]com
- monzo-alerts[.]com
- monzo-card-review[.]com
- monzo-cancellation[.]com
- monzo-accounts[.]com
- monzo-alert[.]com
- monzo-account-review[.]com
- monzo-card-cancellation[.]com
- monzo-notice[.]com
- monzo-cancel-order[.]com
- monzo-review[.]com
- monzo-replacements[.]com
- monzo-replacement[.]com
- monzo-order[.]com
- monzo-plus[.]com
- monzo-limited[.]com
- monzo-dispatch[.]com
- monzo-card-service[.]com
- monzo-dispatched[.]com
- monzo-card-cancel[.]com
- monzo-order-replace[.]com
- revolut-cancel-support[.]com
- revolut-cancellation[.]com
- revolut-cancel-online[.]com
- login-revolut-resolve[.]com
- 91.212.150.0/24
- 93.157.62.0/24
- 93.157.63.0/24