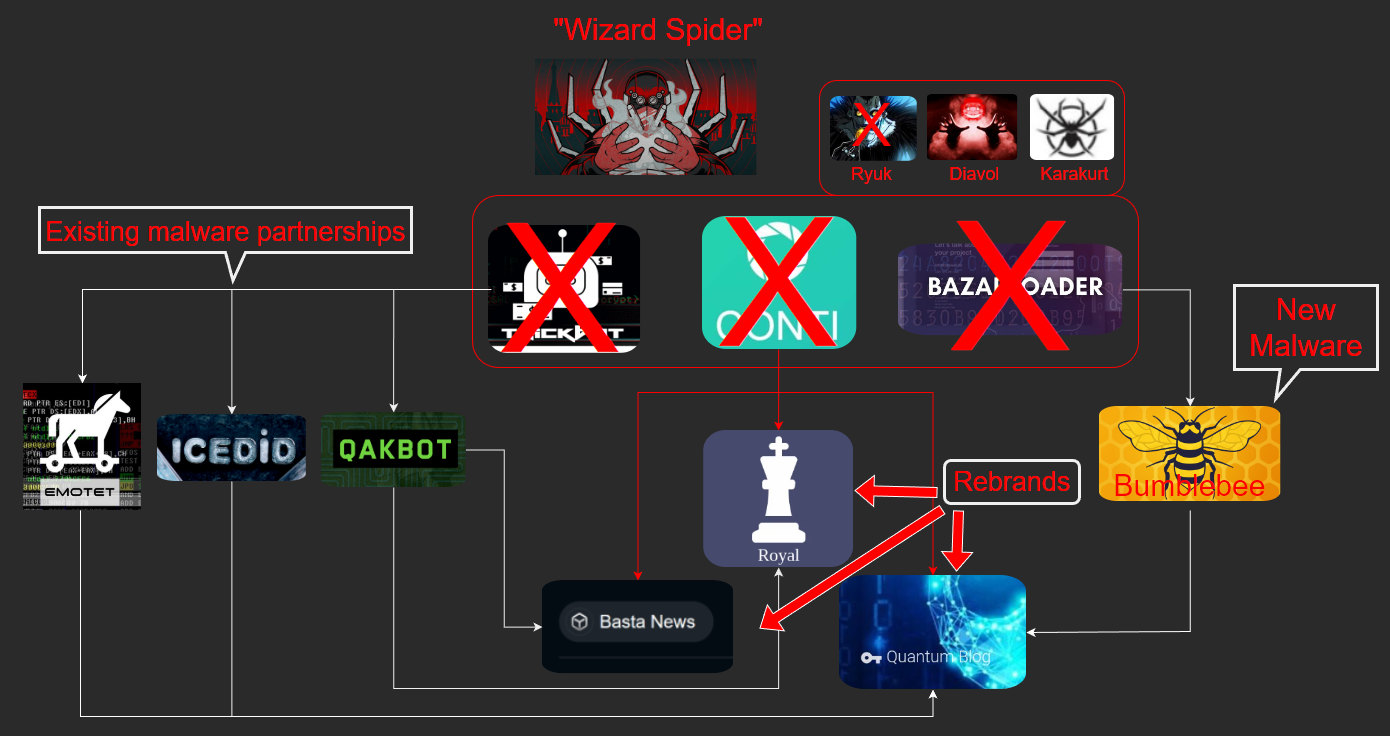
Detecting and Fingerprinting Infostealer Malware-as-a-Service platforms

Cyber threat intelligence largely involves the tracking and studying of the adversaries outside of your network. Gaining counterintelligence about your adversaries' capabilities and weaponry is one of the final building blocks for managing a strong cyber defense. In the pursuit of performing this duty, I have been studying how to discover adversary infrastructure on the internet. One good way of doing this has been via leveraging the scan data available through the popular Shodan search engine. If you've not used it before, Shodan periodically scans the entire internet and makes it available for users to query through. It is often used to monitor networks, look for vulnerabilities, and ensure the security of an organization's perimeter. But we can also use Shodan for tracking the adversaries. Through the process of fingerprinting - that is to identify unique attributes of IPs on the internet - we can find command and control (C2) servers and login panels belongin...